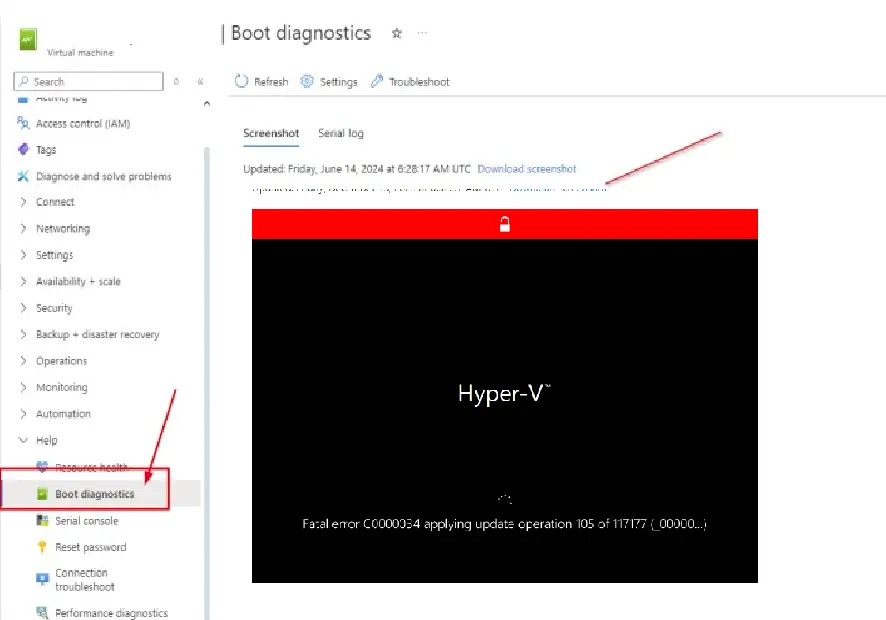
Azure VM: Resolving the c0000034 Fatal Error
One of the critical issues you may encounter when working with Azure Virtual Machines (VMs) is the “c0000034” fatal error. This error typically occurs in Windows operating systems and is usually caused by a corrupt registry hive. The Windows registry is a critical database that stores configuration settings and options for the OS and installed applications. If the registry becomes corrupt, it can prevent the system from booting, leading to serious errors. ...